
In today’s fast-paced digital landscape, efficient log management and analysis are crucial for maintaining robust IT operations. At AIM Consulting, we recognize the challenges faced when troubleshooting extensive Splunk logs.
To help address this, we’ve developed advanced queries that transform these logs into easily readable tables, streamlining the identification process.
Challenges Managing Extensive Splunk Logs
Our clients often encounter difficulties when trying to quickly troubleshoot issues due to the sheer volume of Splunk logs generated. The traditional method of sifting through raw logs can be time-consuming and inefficient, making it hard to pinpoint critical events and notifications.
The Solution: Advanced Splunk Queries
Leveraging Splunk’s powerful querying capabilities, we have devised methods to correlate logs and display them in table formats. This not only enhances readability but also accelerates the troubleshooting process.
A detailed look at our approach:
This is an example of a normal query:
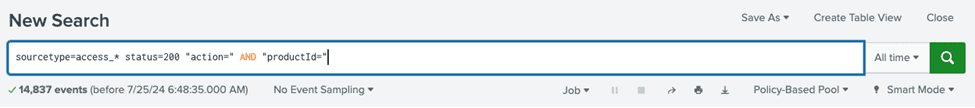
When running a typical query without enhancements, the output can be overwhelming and difficult to interpret.
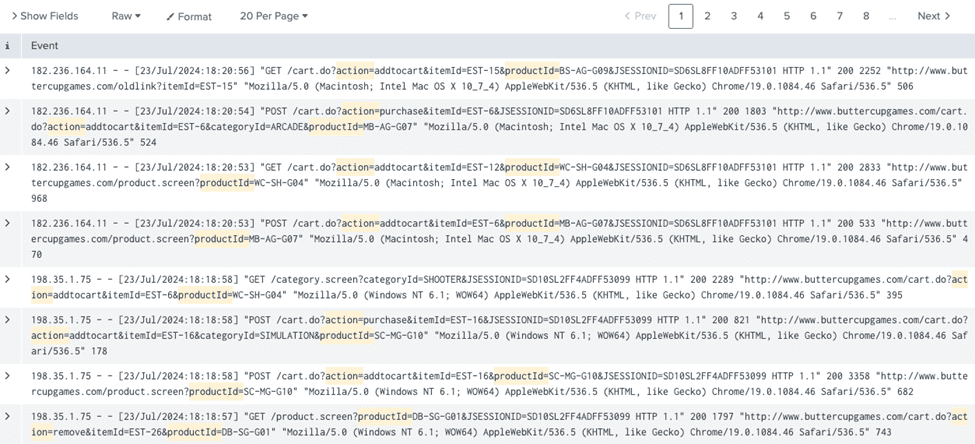
Here is what enhanced querying looks like:

By incorporating regular expressions and table formatting, our enhanced queries provide a clear and organized view of the logs.
The first part helps identify the events we are looking for:
sourcetype=access_* status=200 "action=" AND "productId="while the additional regular expressions and table format provides more readable output:
| rex field=_raw "(?<method>[A-Z]{3,4})\s/cart"
| rex field=_raw "action=(?<action>[a-z]+)"
| rex field=_raw "productId=(?<product>[A-Z]{2}-[A-Z]{2}-[A-Z][0-9]{2})"
| table method, action, productThis enhanced query extracts specific fields and organizes them into a table, making it easier for team members and leadership to quickly identify relevant information.
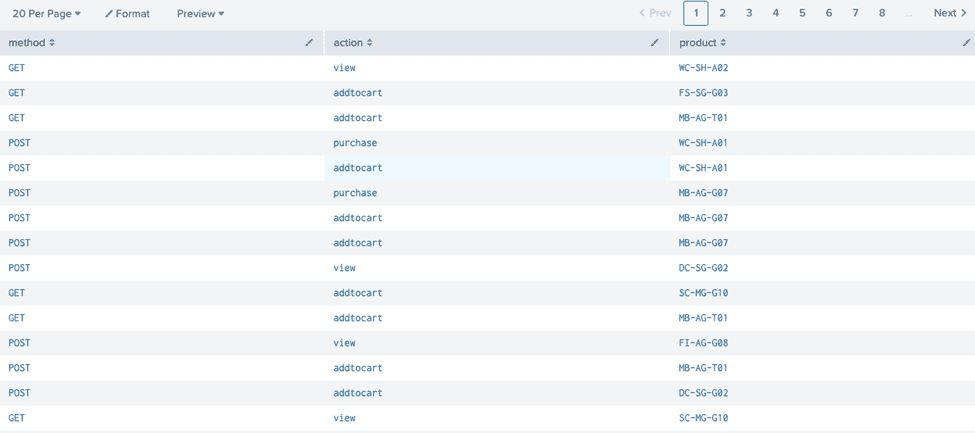
The Impact: Faster Troubleshooting and Better Insights
By converting raw Splunk logs into structured tables, our solution allows for faster identification of key events. This not only speeds up the troubleshooting process but also provides valuable insights to stakeholders across the organization. You can read more about this process in detail in the Splunk Search Tutorial.
Ready to Enhance Your IT Operations?
Our data analytics and and IT operations experts are ready to help you leverage Splunk for better performance and quicker problem resolution.





